Read More: A Deeper Dive into Passkey Technology for IT Professionals
Last week we got some comments on our blogpost that some of our more seasoned IT readers needed some more in-depth knowledge to keep it interesting. You ask, we abide! Have a look at our “Read more” following last weeks blogpost!
In the realm of cybersecurity, the advent of passkey technology marks a significant evolution, particularly in the sphere of authentication protocols. This technology, nascent yet rapidly gaining traction, promises a future where digital security is not just about complex passwords or biometric scans but involves a more integrated, user-friendly, and secure approach to identity verification. Let’s delve deeper into the mechanics, applications, and potential of passkey technology, particularly focusing on what it entails for professionals in IT and cybersecurity.
Understanding Passkey Technology
At its core, passkey technology is a form of authentication that does away with traditional passwords in favor of more secure and convenient methods, such as biometric verification or temporary passcodes sent to trusted devices. These methods are tied to something ‘inherent’ to the user (like a fingerprint or facial recognition) or something ‘possessed’ by the user (like a mobile device).
A passkey can be considered an advanced form of two-factor authentication (2FA), but it goes a step further. Instead of merely adding a second layer of security, it integrates this layer seamlessly into the user experience, often utilizing end-to-end encryption and secure, trusted devices to ensure that the authentication process is both secure and convenient.
The Mechanics Behind the Technology
The technical framework behind passkeys varies depending on the specific implementation, but several key features are generally consistent. Firstly, passkeys often leverage public key cryptography, wherein a public key is freely distributed and used to verify a user’s information while a private key, stored securely on the user’s device, is used to decrypt this information.
Secondly, passkeys often involve secure elements (SEs) within a device, which are tamper-resistant hardware platforms designed to securely host applications and confidential data. SEs ensure that sensitive data, like the private key, is stored in a hardware-isolated environment, making it extremely difficult for unauthorized users or malicious software to gain access.
Real-World Applications and Protocols
WebAuthn, part of the FIDO2 specifications, is a prime example of a protocol that employs passkey-like technology. It’s a web standard published by the World Wide Web Consortium (W3C) that allows servers to register and authenticate users using public key cryptography instead of a password.
WebAuthn is built on the premise that the user’s device creates a new key pair during registration with an online service, and the public key is sent to the server. During authentication, the server sends a challenge, which the device signs with the private key. The server then verifies this signature with the stored public key and grants access if it’s valid.
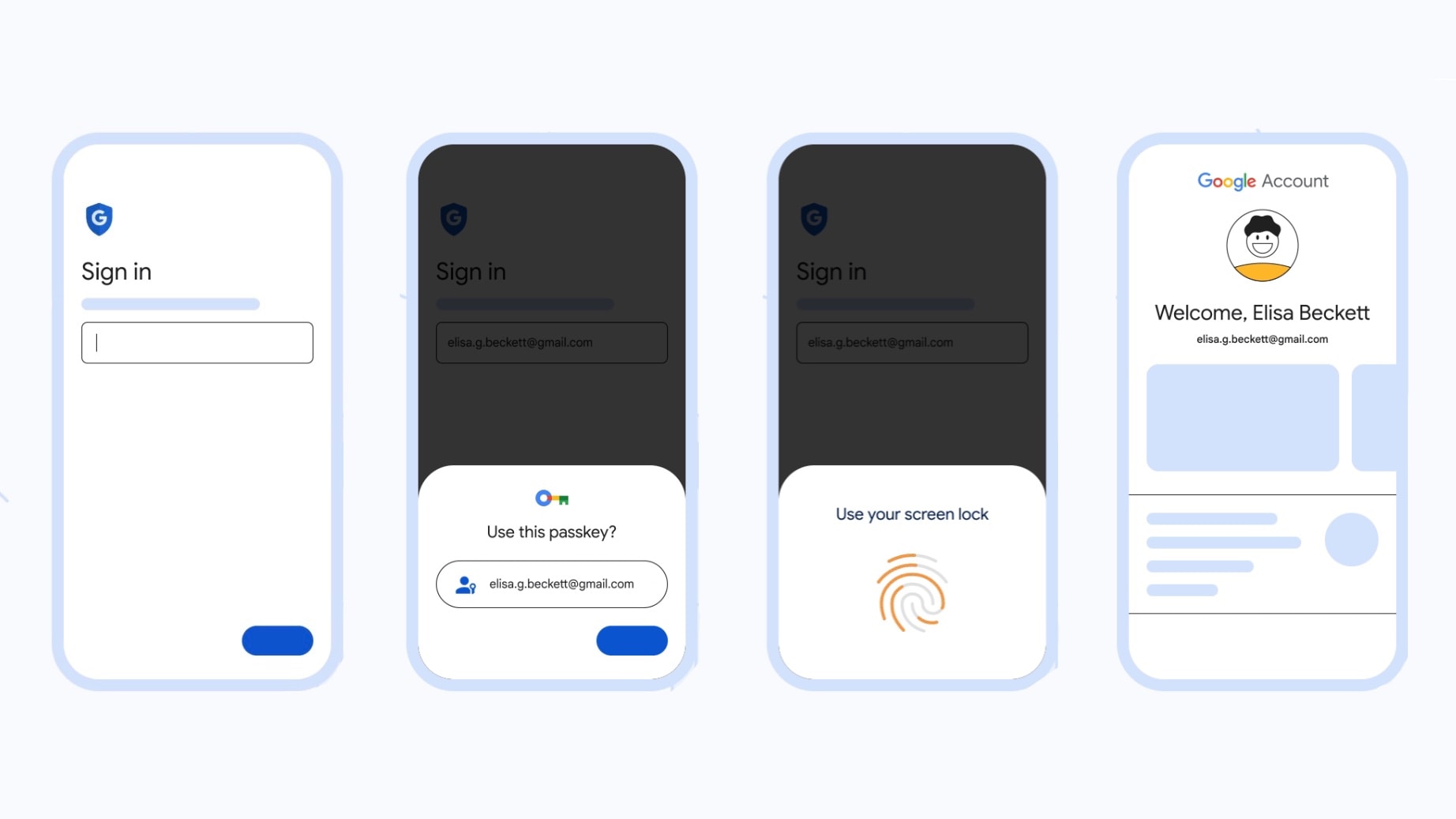
Security Implications and Considerations
From a security standpoint, passkeys are incredibly robust for several reasons. They eliminate the risk of phishing, as there’s no password to steal. They also mitigate the risk of credential stuffing, where cybercriminals use stolen login credentials (usually from a different data breach) to gain unauthorized access to user accounts.
However, no technology is without potential vulnerabilities. If the device storing the private key is compromised, the attacker could potentially have unfettered access to the user’s passkey-protected services. Additionally, if biometrics are used, any system capable of fooling the biometric scanner (like deepfakes or sophisticated replicas) could pose a security risk.
Integrating Passkey Technology with Existing Systems
For IT professionals, integrating passkey technology into existing systems will require careful planning, implementation, and user education. Existing authentication systems may need to be overhauled, and new protocols like WebAuthn may need to be integrated. Extensive testing should be conducted to ensure that the new systems are as secure and user-friendly as possible.
Furthermore, user education is crucial. End-users must understand the importance of keeping their authentication devices secure and reporting any potential security incidents as soon as possible.
Future Prospects and Developments
Looking ahead, we anticipate seeing more integration of passkey technology across various platforms and devices. We might see this technology evolve to include more factors, like behavioral biometrics or geolocation, for even more robust security.
As cybersecurity threats evolve, so too must our defenses. Passkey technology represents the next step in the ever-ongoing battle to keep our digital lives secure. For IT professionals, staying ahead of the curve will mean embracing these new technologies, understanding them deeply, and implementing them effectively.
Here at SecDesk, we’re at the forefront of this technological evolution. Our expertise in cutting-edge cybersecurity solutions positions us uniquely to help companies navigate the intricate landscape of passkey technology. From initial consultations to comprehensive implementation strategies, our team is equipped to guide your transition to a more secure digital authentication ecosystem. Connect with us to learn more about leveraging passkey technology for your business’s cybersecurity needs.
Ready to understand the emerging threats your company will be facing? schedule a free consultation today!


