Understanding ISO 27001 Requirements for Penetration Testing
This is the second post in a series, missed the first one? Find it here.
Achieving ISO 27001 certification is a significant accomplishment for any organization, reflecting a strong commitment to information security management. However, maintaining this certification involves adhering to rigorous standards, including regular security assessments such as penetration testing. This first post in our series aims to demystify and gain understanding iso 27001 requirements for penetration testing, providing clarity on what is needed to stay compliant and secure.
What is ISO 27001?
ISO 27001 is an internationally recognized standard for managing information security. It provides a systematic approach to managing sensitive company information, ensuring it remains secure. This standard includes requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).
Why Penetration Testing is Crucial for ISO 27001
Penetration testing, or ethical hacking, is an essential component of ISO 27001. It involves simulating cyberattacks on your systems to identify vulnerabilities that could be exploited by malicious actors. By proactively identifying and addressing these weaknesses, organizations can enhance their security posture and comply with ISO 27001 requirements.
ISO 27001 and Penetration Testing: The Mandates
Clause 9.3: Management Review
ISO 27001 clause 9.3 mandates that top management must review the organization’s ISMS at planned intervals to ensure its continuing suitability, adequacy, and effectiveness. Part of this review involves assessing the results of security testing, including penetration tests.
Clause 12.6.1: Technical Vulnerability Management
This clause requires organizations to obtain timely information about technical vulnerabilities and assess their exposure to such vulnerabilities. Penetration testing is a proactive method to identify and manage these vulnerabilities, ensuring compliance with this requirement.
Common Misconceptions About ISO 27001 Penetration Testing
Many organizations face confusion regarding what exactly needs to be tested to comply with ISO 27001. Here are some common misconceptions:
- Misconception 1: Only External Systems Need Testing: While external systems are critical, internal systems and applications also need to be tested to ensure comprehensive security.
- Misconception 2: One-Time Testing is Sufficient: ISO 27001 requires ongoing security management. Regular penetration tests are necessary to address new vulnerabilities as they emerge.
- Misconception 3: Passing the Test Ensures Certification: Penetration testing is just one part of the certification process. Organizations must also demonstrate effective management of identified vulnerabilities and continual improvement of their ISMS.
Unsure about your penetration testing needs for ISO 27001? Let’s talk.

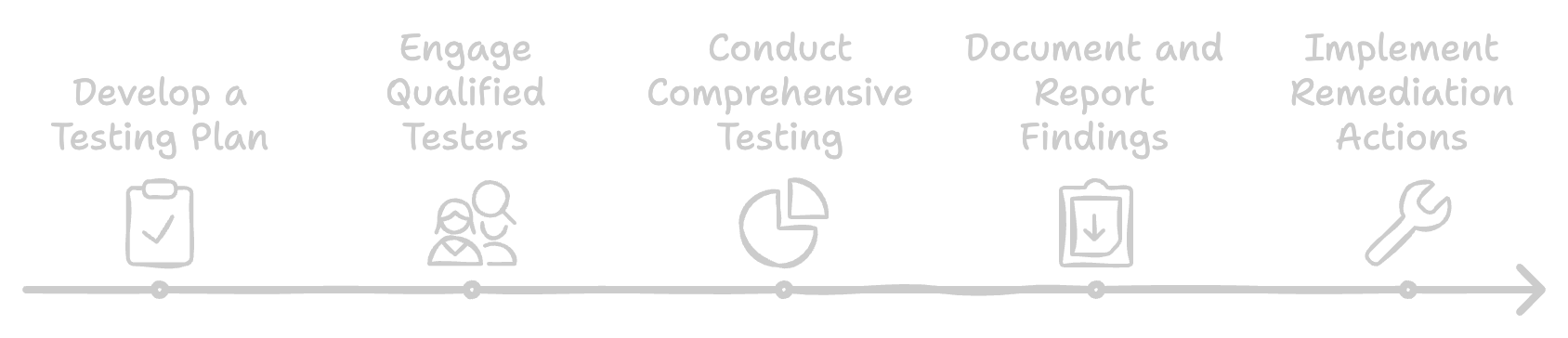
Steps to Align Penetration Testing with ISO 27001
1. Develop a Testing Plan
Create a detailed testing plan that outlines the scope, objectives, and frequency of penetration tests. Ensure that this plan aligns with your ISMS policies and procedures.
2. Engage Qualified Testers
Hire qualified and certified penetration testers who understand the intricacies of ISO 27001. Their expertise ensures thorough testing and accurate identification of vulnerabilities.
3. Conduct Comprehensive Testing
Perform penetration tests on all critical systems, including internal networks, applications, and external interfaces. Ensure that both technical and procedural aspects are covered.
4. Document and Report Findings
Document all findings meticulously. Provide detailed reports that highlight vulnerabilities, their potential impact, and recommendations for remediation. These reports are crucial for management reviews and audits.
5. Implement Remediation Actions
Address identified vulnerabilities promptly. Implement remediation actions and update your ISMS policies to reflect these changes. Continuous improvement is key to maintaining compliance.
The Role of Continuous Monitoring
Penetration testing should not be a one-time activity. Continuous monitoring and regular testing are essential to maintaining a robust security posture. Incorporate automated vulnerability scanning tools to complement manual penetration tests, ensuring comprehensive coverage.
Conclusion
Understanding and implementing the penetration testing requirements of ISO 27001 is vital for maintaining certification and safeguarding your organization’s information assets. By proactively identifying and addressing vulnerabilities, you not only comply with the standard but also strengthen your overall security posture.
Stay tuned for the next post in our series, where we will delve into determining the scope of your penetration test and how to balance thoroughness with practicality.
Interested in Learning More?
Plan a FREE meeting with our team to explore how SecDesk can assist you in navigating the complexities of penetration testing for ISO 27001 certification.
