Decoding the Deception: Homograph Attacks Using Cyrillic Characters
In the constantly evolving landscape of cybersecurity threats, one particularly insidious tactic has been gaining traction: the homograph attack using Cyrillic characters. This type of attack exploits the similarities between Cyrillic and Latin alphabets to deceive users into believing they are visiting familiar websites when, in reality, they are stepping into well-disguised traps set by cybercriminals. This blog post delves deep into the mechanics of homograph attacks, their implications, and how SecDesk helps organizations fortify their defenses against these deceptive strategies.
Understanding Homograph Attacks
A homograph attack, often referred to as an IDN (Internationalized Domain Name) spoofing attack, involves the use of characters from different scripts that look alike to create deceptive domain names. For example, the Cyrillic character ‘а’ (U+0430) looks identical to the Latin ‘a’ (U+0061) but is treated differently by computers. Cybercriminals exploit these similarities to register domains that visually mimic legitimate ones, aiming to fool users into interacting with malicious websites.
The Role of Cyrillic Characters
The Cyrillic script, used in languages such as Russian, Bulgarian, and Serbian, contains several characters that are indistinguishable from their Latin counterparts to the untrained eye. This feature makes it a preferred tool for attackers aiming to create deceptive URLs. For instance, a cybercriminal might register a domain that uses Cyrillic characters to impersonate a well-known brand or institution, leading to potential data theft or malware distribution.
How browsers try to protect the user
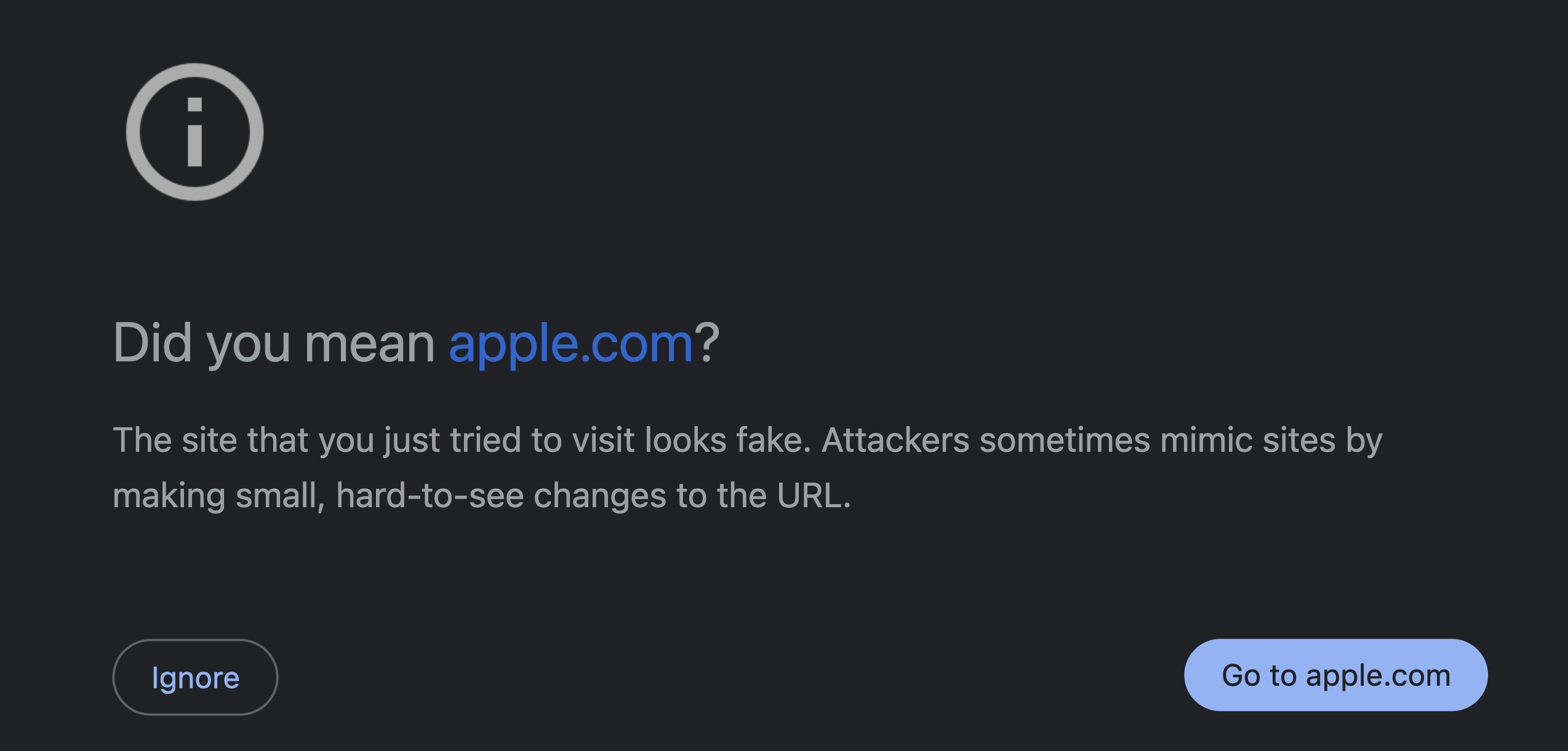
And of course, what is the problem with their protection… Most modern browsers implement “lookalike” protection for highly regarded brands such as apple.com or google.com to just name a few. Going to url’s which use for instance a Cyrillic a or e will show a warning to redirect you to the correct URL as you can see below for the Apple example. However, not many brands are big enough to warrant this kind of protection from Chrome or other browsers, leaving the small brands and their employees without protection from this kind of attack.
Case Study: A Closer Look at a Real-World Attack
Consider a hypothetical scenario where users receive emails from what appears to be their banking institution, asking them to update their account information. The link provided looks correct at a glance because it uses a combination of Cyrillic and Latin characters to mimic the bank’s actual URL. However, clicking on it directs the user to a phishing site where any entered information—be it login credentials or credit card details—is stolen.
SecDesk’s Approach to Combatting Homograph Attacks
At SecDesk, we understand the complexity and danger posed by these attacks. Here’s how we help:
- Awareness and Training: We provide comprehensive training sessions for your employees, educating them about the nature of homograph attacks and how to recognize suspicious URLs.
- Advanced Detection Tools: Our cybersecurity solutions include advanced detection tools that scrutinize URLs for homograph patterns, alerting users before they access potentially dangerous sites.
- Regular Audits and Updates: We conduct regular security audits for your organization’s online assets, ensuring that your defenses stay updated against evolving threats like homograph attacks.
- Multi-layered Security Measures: From DNS filtering to implementing stringent browser security settings, we employ a multi-layered security strategy to safeguard against various vectors of attack, including those involving deceptive characters.
Want to talk security?

Protect Your Organization against Homograph Attacks
Protecting your organization from homograph attacks involves a combination of technical solutions and vigilant practices:
- Implement Punycode Alerts: Ensure that your web browsers and email clients are configured to alert users when a URL includes Punycode, a typical indicator of potential homograph attacks.
- Use Reputable DNS Services: Employ DNS services that offer phishing protection and filter out suspicious domains.
- Regularly Update Security Protocols: Keep your cybersecurity measures up-to-date, adapting to the latest threat intelligence and technological advancements. Need help? Check out our subscription
- Cultivate a Culture of Security: Foster an environment where security is everyone’s responsibility. Encourage employees to report suspicious emails or URLs and provide them with the tools to verify the authenticity of communications.
Conclusion
Homograph attacks using Cyrillic characters represent a sophisticated form of cyber deception, capitalizing on the subtlest vulnerabilities in human perception and script familiarity. By partnering with SecDesk, your organization can enhance its defensive posture, not just technically but also culturally, ensuring that all potential gateways for cyber threats are robustly secured. Want to read more about this kind of attack? Malwarebytes did a great write-up we highly recommend.
Stay vigilant and stay informed, for the digital world’s complexity demands nothing less than our collective and continuous attentiveness.



